The Three XProtects of Christmas
For many years the only tool built into macOS to scan for and remove malicious software was MRT. Its high point came in early July 2019, when Apple repurposed it to remove a hidden vulnerable web server that had been widely installed with the Zoom client. By 2021, Apple had decided to replace MRT with something more modern and capable. The first version of XProtect Remediator was installed in macOS Monterey 12.3 on 14 March 2022, and over the following summer it grew to replace MRT, which was last updated on 29 April 2022, and is now no longer installed with macOS although it may still be obtained as an update.
XProtect Remediator (XPR) is installed and updated outside macOS updates, in the XProtect.app bundle in /Library/Apple/System/Library/CoreServices, in macOS 10.15 Catalina and later. It contains individual executable scanning modules, one of which covers old malware that MRT dealt with. Its first standalone update on 17 June 2022 brought the total of its named malware scanners to eight, and it has grown steadily ever since to a total of 22 in its current version 122.
XPR complements the traditional XProtect, which provides macOS Gatekeeper security checks with a set of detection rules to be applied when scanning apps and executable code before they’re run. Those rules are contained in a separate XProtect bundle alongside XPR, principally in a Yara definitions file, and are used to determine whether to open and execute code at that moment.
Instead, XPR’s scanners are run periodically in the background at frequencies set by XPR itself, according to Apple’s current threat assessments. That’s an improvement on MRT’s scans, that were normally only performed shortly after macOS started up, so provided little protection for Macs that were left running for long periods. Each XPR scan consists of two complete runs, one as the current user, the other as root.
Like XProtect, XPR is updated frequently according to changes in threat. In its early days XPR updates came every two weeks as new scanning modules were developed. Currently updates are released at least once a month, as existing modules are improved, new modules are added, and their scanning frequencies change.
As of XPR version 122, the following scanner modules are included:
Adload, first detected in 2017, added to MRT 1.21 in 2017, one of the original modules in XPR, and still going strong;
BadGacha, added in XPR 91 on 2 March 2023;
BlueTop, added in 108 on 8 August 2023;
CardboardCutout, added in 122 on 19 December 2023;
ColdSnap, added in 99 on 8 June 2023;
DubRobber, added to XProtect on 16 April 2021, and in XPR 62 on 17 June 2022, for XCSSET, a versatile Trojan dropper, first detected in 2020;
Eicar, one of the original modules in XPR, a non-malicious test;
FloppyFlipper, added in 93 on 16 March 2023;
Genieo, detected by XProtect since at least 2013, one of the original modules in XPR, a browser hijacker acting as adware;
GreenAcre, added in 62 on 17 June 2022;
KeySteal, added in 91 on 2 March 2023, exfiltrating keychain contents;
MRTv3, one of the original modules in XPR, covering older malware inherited from MRT;
Pirrit, added to MRT on 6 April 2016, one of the original modules in XPR, malicious adware;
RankStank, added in 96 on 27 April 2023;
RedPine, added in 114 on 12 October 2023, believed to cover TriangleDB malware;
RoachFlight, added in 96 on 27 April 2023;
SheepSwap, one of the original modules in XPR;
SnowBeagle, added in 67 on 21 July 2022;
SnowDrift, added in 68 on 4 August 2022, for CloudMensis spyware;
ToyDrop, added in 64 on 30 June 2022;
Trovi, included in XProtect since 2016, one of the original modules in XPR, a cross-platform browser hijacker;
WaterNet, added in 64 on 30 June 2022.
XPR’s detections, remediations and other findings are reported in the Unified log for all versions of macOS from Catalina, and in Ventura and later as events in Endpoint Security. Otherwise, they aren’t notified to the user in any way. Support for monitoring Endpoint Security is normally confined to third-party commercial security products, although some free-to-use apps including Objective-See’s BlockBlock are now monitoring Endpoint Security events. macOS currently provides no way by which the user is informed of the detection of malware by XPR, or its removal, successful or otherwise.
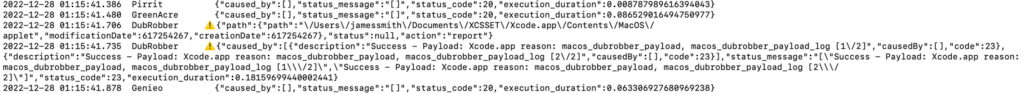
In this log excerpt, XPR has reported that it detected and successfully removed DubRobber/XCSSET.
Occasionally, as with any other malware detection software, XPR reports false positives. Recently, some innocent third-party helpers, including 1Password-Crash-Handler, SnagitHelper2024, crashpad_handler and GoogleSoftwareUpdateAgent, have been triggering false detection reports for BadGacha, for instance. These should be reported both to the third-party developer responsible for that product, and through Apple Support, so that Apple’s security engineers can be informed.
My free SilentKnight checks whether scans have been taking place, and whether any have resulted in detection or remediation. Fuller information, for Catalina and later, is available in my free XProCheck.
macOS Ventura introduced a third type of XProtect, XProtect BehaviorService (XBS), part of Apple’s new Bastion behavioural-based malware detection system. Rather than on-demand or periodic scans of static code, this watches for potentially malicious behaviours, such as attempts to access folders used by browsers such as Safari and Google Chrome. At present, XBS and the Bastion system only record such events and don’t attempt to intervene. Behaviours and exceptions are defined by two files contained within the Resources folder inside XPR’s bundle. Changes in those, in XPR’s scanning modules, and in XProtect’s detection signatures, are reported on this blog for each update released by Apple.
Terms
XProtect provides detection signatures and rules for on-demand Gatekeeper checks to determine whether code is safe to run.
XProtect Remediator performs periodic background scans to look for known malicious software, and tries to remove any that it detects.
XProtect BehaviorService provides behavioural rules and lists of exceptions for Bastion to monitor potentially malicious behaviour.
If you fund, develop or distribute malicious software, I suggest that this Christmas you should read Dante’s Inferno, and Charles Dickens’ Christmas Carol, so you can prepare for your future.
For those engineers in Apple’s SEAR, others who undertake Mac security work for other organisations, and independent researchers, I thank you for all your work to protect us in the past, present and future: merry Christmas!
I’m grateful to Mike and others for contributing information used above.