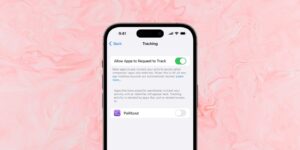
Last Week on My Mac: magic updates
In case you didn’t notice, Apple flew a firmware update under the radar last week. It made no announcement other than slipping out a security release note recording the bug this update addresses. This update flew so far below the radar that it wasn’t available through Software Update, and made no record of its installation except in the firmware of Apple’s Magic Keyboards. The only way to tell if your keyboard has been updated is to check via Bluetooth settings. This is simplest by holding down the Option key as you open the Bluetooth menu from the right end of the menu bar: you should now see a Firmware Version of 2.0.6.
This isn’t the only fix, though. macOS Sonoma’s 14.2 update contained another, where a Bluetooth keyboard spoofing attack has been mitigated by “improved checks”.
Looking at the two notes, Apple quotes two different CVEs to them: CVE-2023-45866 for that fixed in macOS 14.2, and CVE-2024-0230 for that fixed in the keyboard firmware update. Rumour has it that the vulnerability found in Magic Keyboards is also present in older Apple Bluetooth products, and in the Magic Mouse, leading to questions as to why no firmware updates have been provided for products other than those listed by Apple, as:
Magic Keyboard
Magic Keyboard (2021)
Magic Keyboard with Numeric Keypad
Magic Keyboard with Touch ID
Magic Keyboard with Touch ID and Numeric Keypad.
The best way to find out what’s going on is to refer to the definitive account by Marc Newlin of SkySafe, who discovered and reported these vulnerabilities in the first place. I strongly recommend reading that account: it’s a fine example of clarity that guides you through the complexities of Bluetooth.
Marc Newlin details two separate vulnerabilities:
CVE-2023-45866, affecting multiple operating systems and fixed in macOS 14.2, allows an attacker to pair a spoof keyboard without authentication or user confirmation. In macOS, this is ‘zero-click’, but has to be attempted when the Mac is trying to connect to a paired keyboard, commonly after disconnecting its charging cable.
CVE-2024-0230, believed to be fixed in the keyboard firmware update last week, involves an exploit that can lead to the extraction of the Bluetooth link key, via the keyboard’s Lightning port, unauthenticated Bluetooth when the keyboard is unplugged from the Mac, or through the USB port on the Mac.
Both of these require the attacker to be physically present, have access to the keyboard and/or Mac, or to be able to observe disconnection of the keyboard charging cable. These are not remote attacks.
Although serious vulnerabilities, the circumstances in which they could be exploited are limited. If you’re using a Magic Keyboard in an enterprise or educational setting, particularly in classrooms, labs or cubicles, then they are real threats. For SOHO or home users, unless you envisage a potential attacker getting close enough to your Mac, they probably aren’t feasible in the slightest.
Marc Newlin reports finding the CVE-2024-0230 vulnerability in the Magic Mouse 2 as well as four variants of the Magic Keyboard, although Apple hasn’t announced any firmware update for that mouse yet, and tests don’t appear to have been performed on older Bluetooth keyboards or mice, nor on either model of Magic Trackpad.
The macOS vulnerability in CVE-2023-45866 has so far only been addressed in Sonoma, and hasn’t been fixed in Ventura or Monterey, nor has it been tested for in macOS 11 or earlier.
For enterprise users, the threat and keyboard firmware update must be making a lot of work. For the rest of us, while it’s important to ensure that our Macs and their Bluetooth devices are properly protected, the only important message is to underline yet again that, if your Mac isn’t running the current version of macOS, it really isn’t secure at all.