A brief history of keychains
Passwords and other secrets were little-used until the arrival of email and the Internet. Secure storage for them in keychains was developed for the PowerTalk mail engine in Apple Open Collaboration Environment (AOCE), and was first released in about September 1993, probably in System 7.1.1. When AOCE was dropped from Mac OS 8, keychains languished until their revival later that decade, and were probably first supported by the System in around 1999 in Mac OS 8.6.
Those early keychains were the ancestors of what’s now referred to as file-based keychains, in contrast to the data protection keychain that can be shared in iCloud. Although macOS Sequoia still supports classic keychains, their use was discontinued with the introduction of Mac OS X in 2001, when they were replaced with newer keychains supported by the SecKeychain API.
SecKeychains gained full support in Mac OS X 10.2 Jaguar in 2002, and ever since have provided the central login keychain still used in Sequoia over 20 years later. These are encrypted databases containing login credentials and other secrets. Each keychain can be unlocked using a single password, with that of the login keychain being the same as the user’s login password, enabling it to be unlocked following login.
With the introduction of iPhones and their iOS operating system, they didn’t use SecKeychains, but a new and more secure relative known as the Data Protection keychain, with a separate SecItem API. Although support for that was added in Mac OS X 10.6 Snow Leopard in 2009, it wasn’t until OS X 10.9 Mavericks in 2013 that Macs started using Data Protection keychains for their iCloud Keychain. Two years later, with OS X 10.11 El Capitan, SecKeychains and their ancestors were formally deprecated, although much of their APIs still remain.
Throughout Mac OS X and into macOS, the bundled tool for maintaining keychains has been Keychain Access provided in /Applications/Utilities. With the arrival of the iCloud Keychain, Safari provided access to passwords stored in the iCloud Keychain, and that was later augmented in a Passwords item in System Preferences and Settings.
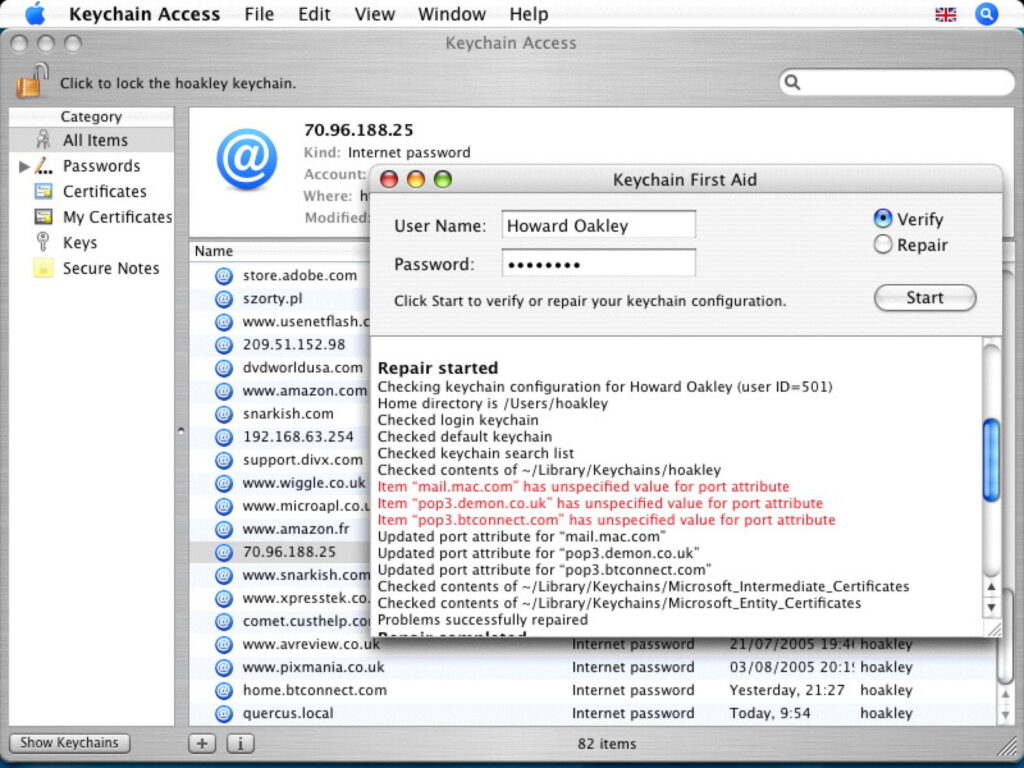
Earlier versions of Keychain Access, such as that seen here in Mac OS X 10.4 Tiger in 2005, provided a valuable First Aid tool to verify and repair keychains. That was dropped some years ago.
After the introduction of iCloud Keychain, the login keychain has steadily lost importance. Here it’s seen at its zenith in Mac OS X 10.6 Snow Leopard.
This shows the login keychain again, in Keychain Access from OS X 10.10 Yosemite in 2014.
macOS Sequoia brought a dedicated app Passwords that only works with the Data Protection keychain, and relegated Keychain Access to /System/Library/CoreServices/Applications, where it can still be used to work with traditional file-based keychains as well.
login keychain
For each user, their default personal file-based SecKeychain is the login keychain, located in ~/Library/Keychains/login.keychain-db. This is unlocked automatically when the user logs in as it has the same password as that user account. It’s here that each user can still store certificates, secure notes, etc. for general use on that Mac.
Although kept unlocked, readable and writeable while the user is logged in, that doesn’t guarantee access to its contents. If an app makes a call to the macOS security system to retrieve a stored password for its use, that system determines whether the app is trusted to access that information, and whether that keychain is locked. Assuming the password is stored there, the app is trusted, and the keychain is unlocked, then the password is retrieved and passed back to the app. If the app isn’t trusted or the keychain is locked, then the security system, not the app, displays a distinctive standard dialog asking for the password to that keychain to authenticate before it will provide the password to the app.
Access to secrets is determined by the security system, the specific access it grants to an app, and to individual items in that user’s keychain. At its most restrictive, the system can limit all other apps from accessing a particular secret in the keychain, but specific secrets can also be shared across several different apps.
System keychains
For the system, there two two vital groups of keychains:
in /System/Library/Keychains, in the SSV, are SystemRootCertificates and others providing the set of root security certificates for that version of macOS;
in /Library/Keychains is the System keychain and others providing certificates and passwords required for all users, including those to gain access to that Mac’s Wi-Fi connections.
Data Protection keychain
Since OS X 10.9, Macs have also had one and only one Data Protection keychain that’s accessed using the SecItem API. If you share your keychain in iCloud, this is the local copy of that shared keychain and is known as iCloud Keychain; if you don’t share it in iCloud, then it’s known as Local Items instead. The local copy of this is normally stored in ~/Library/Keychains/[UUID]/keychain-2.db, where the UUID is that assigned to that Mac.
This Data Protection keychain stores all the standard types of secret, including internet and other passwords, certificates, keys and passkeys. Prior to macOS 11, it only synchronised internet passwords using iCloud, but from Big Sur onwards it synchronises all its content, including passkeys, which have now become first class citizens. Unlike file-based keychains, secrets in the Data Protection keychain can be protected by the Secure Enclave in T2 and Apple silicon Macs, and can therefore be protected by biometrics including Touch ID, and Face ID on iOS and iPadOS. Hence they’re required for passkeys, which can’t be supported by traditional file-based keychains.
Future
Much as Apple wants to support only the Data Protection keychain in macOS, there are still many that rely on the login and other file-based keychains. SecKeychain will thus remain supported reluctantly until macOS can finally call it a day on keychains that originated well over 25 years ago.
References
Apple TN3137: On Mac keychain APIs and implementations
Apple Keychain Services
