What are app entitlements, and what do they do?
Entitlements are settings baked into an app’s signature that enable it to do things that otherwise wouldn’t be allowed. Many let App Store apps do things their sandbox wouldn’t normally permit. Others give access to features that are controlled by privacy protection, so may be used by apps that aren’t sandboxed. A few enable apps specially approved by Apple to use features in macOS that aren’t generally available, such as working with APFS snapshots.
One way to run third-party apps in relative security is to confine them to a tightly restricted environment, a sandbox. That denies them the ability to access storage or other resources outside those dedicated to it in its sandbox. That’s too restrictive for the great majority of apps, which need to be able to open and save documents to folders such as ~/Documents, so entitlements specify which sandbox restrictions they’re allowed to break. In the case of opening and saving documents outside the sandbox, the entitlement is named com.apple.security.files.user-selected.read-write, and gives that app read and write access to files the user has selected in a standard macOS Open or Save dialog. Apple requires that all apps distributed through its App Store run in their own sandbox, so they all claim entitlements to be able to work beyond that.
Sandboxed apps all have their own entitlement to their sandbox, com.apple.security.app-sandbox, which isn’t used by apps that are notarized but not sandboxed. Whether sandboxed or not, an app might need access to the Mac’s camera, and for that it will need an entitlement named com.apple.security.device.camera.
Thus, entitlements fall into groups:
Those that can be used by any app that wants access to controlled features, depending on whether it’s sandboxed or not.
Those that give access to macOS features that have to be approved by Apple.
Those that are private to Apple’s own apps and can’t be used by third-parties.
Viewing entitlements
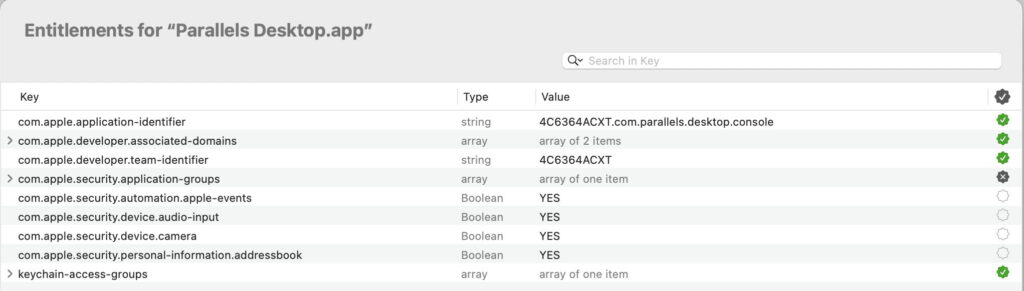
The Finder and other macOS utilities don’t reveal whether an app runs in a sandbox, nor list its entitlements. For that you’ll need a third-party tool such as Mothers Ruin’s Apparency.
Apparency’s Entitlements pane lists all those baked into that app’s signature. My own free Taccy also lists entitlements, but for this purpose Apparency is the better tool by far.
Apps that aren’t sandboxed, only hardened and notarized, will only have entitlements if they need to access privacy-protected features, or use restricted features in macOS. In many cases, that means they will have neither entitlements nor a provisioning profile.
com.apple.security
These give an app access to files and features that are restricted, either by the sandbox, or by privacy protection.
Sandbox controls
These are options that extend an app’s abilities beyond the sandbox, starting with the entitlement that sets the sandbox in the first place. They aren’t used by apps provided outside the App Store that are only notarized and not sandboxed. Apple provides fuller details of the sandbox here.
Examples include:
com.apple.security.app-sandbox runs the app in a sandbox, and is standard for all sandboxed apps
com.apple.security.files.user-selected.read-write gives read and write access to files the user has selected in a standard macOS Open or Save dialog
com.apple.security.files.bookmarks.app-scope gives access to security-scoped bookmarks with app scope
com.apple.security.files.bookmarks.document-scope gives access to security-scoped bookmarks with document scope
com.apple.security.network.client allows it to open outgoing network connections
com.apple.security.print allows it to print.
Privacy controls
These give access to information, devices and features that are controlled by the privacy features in macOS, enforced either by Location Services or by TCC. These are used by any third-party app, whether supplied through the App Store or not, and include:
com.apple.security.personal-information.addressbook gives access to the content of the address book
com.apple.security.personal-information.location gives access to location data from Location Services
com.apple.security.device.camera gives access to the camera
com.apple.security.device.microphone gives access to the microphone
com.apple.security.automation.apple-events enables automation using AppleEvents.
These normally have a corresponding list in Privacy & Security settings.
com.apple.developer
These entitlements can only be granted by Apple, and control access to macOS features that aren’t generally available. Among the most common are:
com.apple.developer.endpoint-security.client enables it to monitor system events for potentially malicious activity using Endpoint Security
com.apple.developer.persistent-content-capture is required for a Virtual Network Computing (VNC) app to have persistent access to screen capture
com.apple.developer.driverkit gives an extension permission to run as a user-space driver
com.apple.developer.vfs.snapshot gives access to snapshot features
com.apple.vm.networking allows virtual network interfaces without their having to escalate privileges to the root user, typically in bridged networking.
com.apple.private
These are private to Apple’s own apps, and encompass many other com.apple entitlements that aren’t documented for third-party developers. Examples include:
com.apple.private.applemediaservices
com.apple.private.dmd.policy
com.apple.private.octagon
com.apple.authkit.client.private
com.apple.duet.activityscheduler.allow.
Some appear self-explanatory, others are opaque.
Command tools and standalone executables
Although Mach-O binaries such as command tools and daemons can be hardened and signed, thus can be notarized, they can’t have a provisioning profile embedded, so can’t have entitlements. Apple recommends working around this by wrapping them in an app-like structure, as explained here.
Entitlements for access to features controlled by privacy protection rely instead on the attribution chain to determine whether they’re entitled. Thus a command tool called by an app isn’t expected to have the entitlement, but the app calling that binary is.
Stripping signatures
Because entitlements are baked into the signature, if you were to strip the signature from an app, that would remove all its entitlements. For a sandboxed app, that might not be fatal, but for most other types of entitlement, that could render the app non-functional. Resigning the app with an ad hoc signature wouldn’t help either.
References
Apple’s Entitlements documentation
Tech Note 3125 on provisioning profiles for code signatures
If you can’t find an entitlement in any of those lists, try looking in Jonathan Levin’s database of all known entitlements for iOS and macOS, which is as comprehensive as we’re likely to get.