What to do when macOS won’t let you unmount a volume
It always happens when you’re in a rush to eject an external disk, or when you’re trying to run First Aid in Disk Utility: you’re told that a volume or disk can’t be unmounted or ejected because “one or more programs may be using it” or similar excuses. Not that macOS gives you the slightest idea as to which programs are. This article looks at what you can do next.
Whatever you do, don’t just pull the cable of an external disk: not only will your Mac complain, but you could end up damaging the contents of its files, or even the file system on that volume.
Force eject
This is often offered as an option in the dialog, and if it’s available it’s worth trying if you don’t have the time to carry out a more orderly unmounting. macOS should then identify the processes that are accessing the disk, and terminate their access. That can take time, and seldom appears successful even if you allow a minute or two for it to complete. However, when it does work, it’s likely to be the simplest solution.
Try again
In Disk Utility, this is usually the best option, and if necessary you can try several times. You should also double-check that you’re trying the correct volume: if it’s one of the current boot volume group, System or Data, then you’re better off running First Aid in Recovery mode anyway.
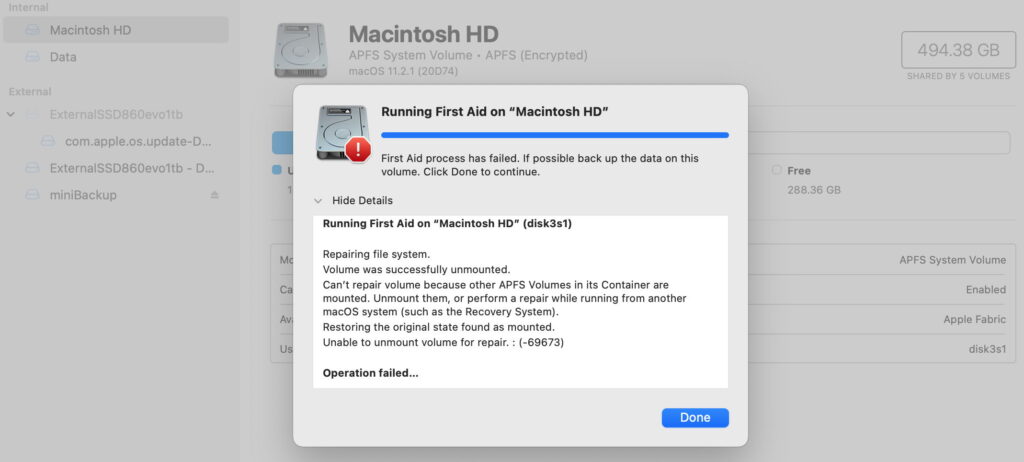
Getting nowhere
When all else fails, the next step is to identify what’s using files on that volume or disk, so you can decide whether to force quit that process in Activity Monitor. Don’t do that blindly, as you could end up killing processes that your Mac does need to run.
To discover which files are open on any volume, use the command
sudo lsof /Volumes/myVol
where myVol is the name of the volume. If you’re unsure how to enter a volume name containing a space, locate it in the Finder’s listing for your Mac, and drag and drop that into Terminal. Once you’ve entered that, type your admin user password at the prompt, and you’ll see a list with entries like
mds 367 root 33r DIR 1,28 192 2 /Volumes/External2
mds 367 root 35u REG 1,28 0 87 /Volumes/External2/.Spotlight-V100/Store-V2/3DD5246F-9AEA-4F0E-9A53-AA63783C3C70/journalExclusion
which are the files and directories open on that volume. This needs to be run using sudo, as otherwise you won’t see any files that are opened by processes running as root, which are most often the culprits. Some recommend using grep, but that shouldn’t be necessary, as lsof is capable of its own filtering.
The information given about each open file contains, from the left:
an abbreviated name of the command associated, here mds, the Spotlight metadata server;
the open mode, as the single character following two digits, e.g. 33r is opened for read access only, while 35u is opened for read and write access;
the type, DIR meaning directory, and REG meaning a regular file;
the full path to the file or directory.
If you’d rather use an app, then my personal favourite is Sloth from here. Although it’s not notarized, it does everything that I’d want in terms of matching lsof or fuser‘s features. Most importantly, if you click its padlock at the lower right and authenticate, it will show all processes running as root.
If your Mac is running Sequoia, getting Sloth through its security checks is a bit of pain (and intentionally so). You can do this the ‘official way’ by downloading the app, unZipping it, and moving it into your Applications folder. When you try to run it, that will be denied and you’ll end up having to give it your individual authorisation in Privacy & Security settings. Alternatively, you can run the risk and cheat by stripping the com.apple.quarantine extended attribute from its Zip file first, so it doesn’t undergo full first run checks. Although that may be simpler, it also forces you to place complete trust in the app you’ve downloaded.
Once you know which processes are accessing files on that volume, you can decide whether to open the listing in one of Activity Monitor’s views, such as CPU or Disk, select that process, and click on the Stop tool to kill it.




