Manage privacy protection for network devices and others
So far in this series explaining how you can control access to potentially sensitive features and data in macOS, I have covered the following topics:
Gaining access to privacy-protected folders,
Managing privacy-protected devices,
Managing access to location information.
This article rounds those off with a brief survey of other privacy controls, including an account of the newest of them all, over local network devices.
Additional privacy controls
There are several controls over specific classes of data, including
Calendars
Contacts
HomeKit
Media & Apple Music
Photos
Reminders
Focus
Motion & Fitness.
These are normally the preserve of specialist apps that are required to seek your explicit consent, and are controlled in their own entries in Privacy & Security settings. General access to their files can be given through Full Disk Access as well, where appropriate.
There’s a final group of controls whose purposes overlap more, and as a result may appear confusing:
Passkeys Access for Web Browsers, required if you want a third-party browser to use passkeys for authentication.
Accessibility, allowing control over your Mac, as in Automator and AppleScript. These can be added manually.
App Management, allowing an app to update or delete other apps, which can be added manually.
Automation, allowing control over other apps, so giving access to the data and documents within controlled apps, and to perform actions with them, but that doesn’t include Automator itself.
Developer Tools, required to run software locally that doesn’t meet macOS security rules such as the requirement for notarization. This is primarily for developers, and can be added manually.
Local Network, allowing access to network devices, as described below.
Remote Desktop, allowing access to the contents of the screen.
As with other controls, these are all managed by TCC, and their individual lists can be cleared and reset using the command
tccutil reset [list]
where [list] is one of the following:
Accessibility
AddressBook (for the Contacts list)
AppleEvents (for the Automation list)
Calendar (note the singular, for the Calendars list)
ContactsFull
DeveloperTool
FocusStatus
MediaLibrary
Motion
Photos
Reminders
RemoteDesktop
ScreenCapture
Local network privacy
This is one of the latest, introduced in macOS Sequoia. Although common to macOS, iOS, iPadOS and visionOS, it doesn’t work the same in each. It’s explained in TN3179 of 31 October 2024, and seems likely to evolve in the future.
Many apps access remote locations outside your local network; currently there are no privacy restrictions imposed on those, but code that accesses devices inside your local network, including your router, comes within the scope of this control. Some apps that work with devices on your local network do so using code that’s automatically given local network access because it’s a Launch Daemon or running with root privileges. Together with command line tools run in Terminal or over SSH, those aren’t controlled by TCC.
Regular apps and other code that attempt to access the local network will result in the user being asked to give their consent. While apps are invited to provide the text to be used in this dialog, in an NSLocalNetworkUsageDescription in their Info.plist, at the moment that isn’t enforced as a requirement, nor is there a required entitlement. You’re thus unable to verify whether an app should be expected to request access to local network devices.
This can apply to any app that tries to list other devices on the local network, whether over wired Ethernet or Wi-Fi. Those that also access Bluetooth will additionally request that, in a separate consent dialog.
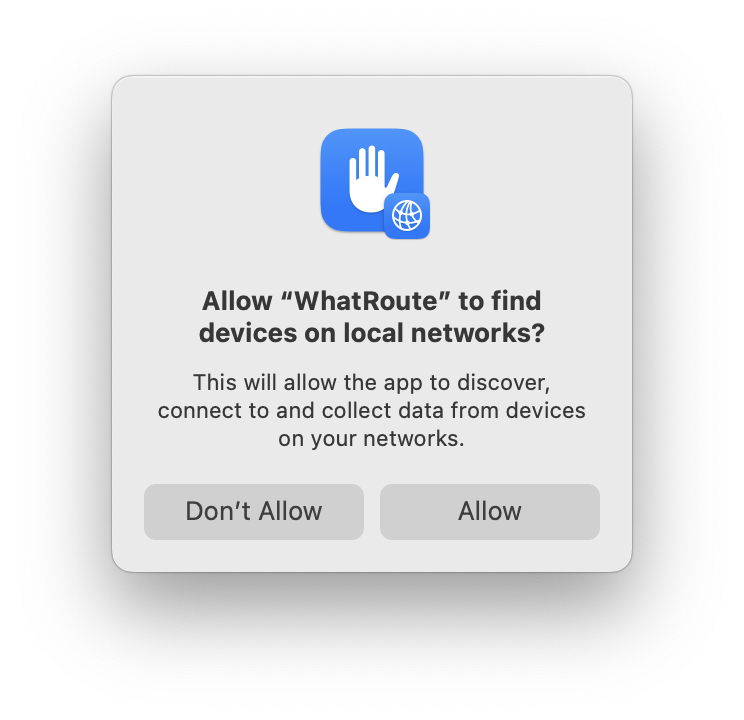
Those who know Bryan Christianson’s excellent network utility WhatRoute may already have discovered that opening it for the first time in macOS Sequoia results in a privacy consent dialog. This might appear puzzling for an app that’s all about Internet connections, but as it does look at your router and can be used within your local network, macOS includes it within this new privacy category.
For the moment, Apple doesn’t appear to provide a service name that can be used with tccutil to reset its privacy settings, and disabling them in System Settings doesn’t remove them from the list. If you really need to reset that list, you’ll have to use
tccutil reset All [appID]
with the appID of each app that has already been given access.
Finally, because of the problems with network controls in early versions of macOS Sequoia, don’t rely on local network privacy in releases prior to 15.3.
Summary: local network privacy
Sequoia introduces consent dialogs for access to devices on the local network, including routers, via Ethernet or Wi-Fi.
This doesn’t apply to connections made to remote locations on the Internet.
Launch Daemons, code running with root privileges and command tools in Terminal or via SSH aren’t affected.
Access by other apps may result in a consent dialog, and an entry in Privacy & Security settings.
Currently tccutil can’t reset all local network privacy settings in a single command.


