What malware can macOS remove?
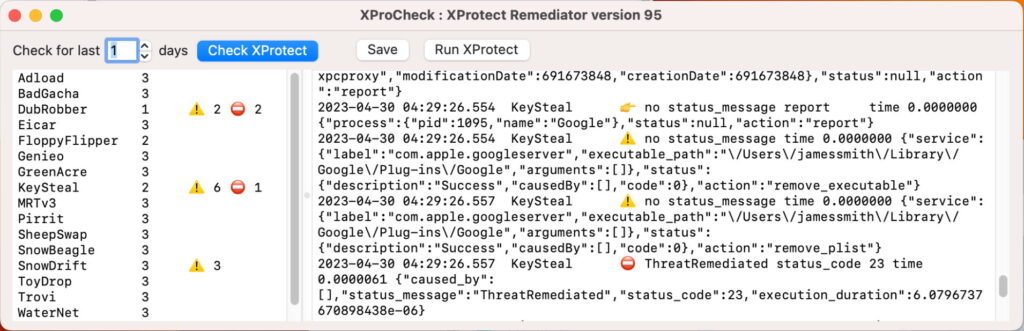
Until two years ago, Apple’s Malware Removal Tool, MRT, was all that macOS had to deal with any malicious software that got onto your Mac. While Gatekeeper and its XProtect signatures can detect known malware when it tries to run, it was left to MRT to seek it out and remove it when possible. This changed in the summer of 2022, when Apple brought its new XProtect Remediator (XPR) up to full speed as the successor to MRT. This article updates information about which malware it scans for, and tries to remediate.
Alden has recently brought substantial advances in the understanding of how XPR’s scanning modules work, by uncovering some of their internal Yara-based detection signatures. These confirm the suspicion that XPR uses Yara definitions for at least some of its detection, although in these cases it embeds them in its scanning modules, rather than using those supplied in XProtect’s data. Combining Alden’s results with existing knowledge, we can now account for 14 of the 23 scanning modules in the current version of XPR.
Adload is an old adware and bundleware loader dating back to 2016 that has a track record of rapid change, enabling it to evade static detection. It normally achieves persistence through a bogus service installed in ~/Library/LaunchAgents/, and Phil Stokes gives fuller details here.
BadGacha remains unidentified, but frequently reports false positives for helper apps in non-malicious apps.
BlueTop is a bogus WindowServer app that was part of a Trojan-Proxy campaign investigated by Kaspersky in late 2023.
CardboardCutout remains unidentified.
ColdSnap is known better as SimpleTea, a cross-platform component that was part of the 3CX supply-chain attack.
Crapyrator has been identified as BkDr.Activator, found in many torrents of cracked apps such as MarsEdit, DaisyDisk, and SpamSieve. It uses sophisticated methods, characteristically installing Activator.app in the main Applications folder, prompts for a password and uses that to disable Gatekeeper checks, then kills Notification Centre to cover its tracks. Further details are given here.
DubRobber is known more generally as XCSSET, a versatile and troubling Trojan dropper that changes frequently to escape detection.
Eicar isn’t malware at all, but a standard non-malicious test of detection methods.
FloppyFlipper remains unidentified.
Genieo, also known as MaxOfferDeal, is another old hand that changes frequently to escape detection. This is so well-known that it qualifies for its own page in Wikipedia.
GreenAcre remains unidentified.
KeySteal, as its name suggests, exfiltrates the contents of keychains. Although it first appeared at least three years ago, it seems to have reappeared in autumn/fall 2022, and has been described in full detail by Luis Magisa and Qi Sun of Trend Micro. It has been found as a malicious version of the ResignTool app, used to change code signatures. It can come correctly signed, and has been delivered in a signed Installer package.
MRTv3 is a collection of malware detection and remediation items inherited from Apple’s old Malware Removal Tool, MRT.
Pirrit has also been known in many different variants and forms since it first appeared in 2016. For a long time it posed as a Flash Player installer, although it has moved on since then. It has been overviewed recently by Paloalto Networks.
RankStank is another malicious app at the centre of the 3CX supply chain attack, where it’s found in the 3CX Desktop App, and has been attributed to the Lazarus Group.
RedPine is believed to cover TriangleDB malware, sophisticated spyware that has been targeted primarily at iOS devices using malicious Messages.
RoachFlight remains unidentified.
SheepSwap remains unidentified.
SnowBeagle remains unidentified.
SnowDrift is CloudMensis spyware, another sophisticated malicious app that may masquerade as WindowServer.
ToyDrop remains unidentified.
Trovi is a cross-platform browser hijacker that can affect Safari and others.
WaterNet remains unidentified.
I hope this makes more sense from what you see in XProtect Remediator, and thank Alden, Phil Stokes and others who been decoding Apple’s bizarre names.